TrustiPhi provides specialized hardware-level security engineering, advanced design and security architecture consulting.
NEWS – SanCloud Delivers Micron® Authenta™ IoT Cybersecurity Breakthrough with TrustiPhi Integration
2 Technical Videos – Triathlon Demo + Authenta™ Use Cases / from Micron® Tech Field Day 8
The IoT is undersecured. Connected devices need hardware-level security.
TrustiPhi has the solutions that OEMs, device operators, and service providers need.
TrustiPhi takes clients through architecture, design, and deployment to build hardware-level security into products. We build and deliver on the roadmap to IoT device fleet security, compliance, and new business models.
TrustiPhi works with OEMs to enable security in many kinds of IoT devices for use in energy production, defense and military, automotive, and health care – as well as manufacturing, telecommunications, and other fields.
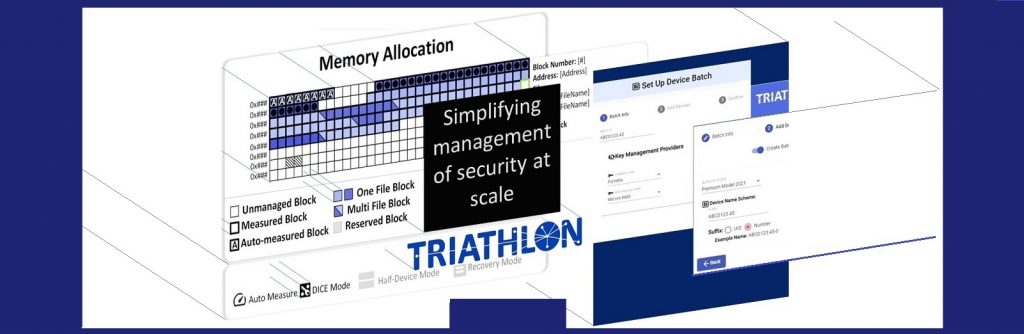
Take advantage of full cryptographic security in flash memory. Our Triathlon platform puts Micron Authenta into action, handling everything from provisioning to ongoing secure OTA updates and device integrity monitoring.
Simple, affordable, low-risk steps to enable and easily manage security in fleets of IoT devices, from manufacturing an endpoint product through deployment, and a more secure and profitable device operating life.

The IoT Security Management Platform
Easily secure the life cycle for fleets of IoT devices.
TriathlonTM from TrustiPhi is for
Infrastructure Operators and Vendors
TriathlonTM is an essential mainstay in your drive to augment your products with strong security that begins before bootup, at the hardware level. Triathlon makes it simple to add mass-scale, automated secure OTA firmware updates, and device integrity monitoring with exceptions reporting for fast identification of tampering and compromises.
Device Owners and Operators
Manage hardware-based security across fleets of connected devices. Easily set up and conduct secure over-the-air (OTA) firmware and software updates at scale, and deliver valuable services like 24/7 monitoring of device integrity. Enable the transformation of your product from a physical device to an ongoing revenue stream.
OEMs and Device Manufacturers
Leapfrog product development delays and drive down risks by embedding Micron Authenta, then activating and configuring it with TriathlonTM from TrustiPhi.
The IoT has lacked an easy-to-use, massively scalable management platform to help securely:
* manufacture
* provision
* deploy
* update and
* monitor integrity of
IoT endpoints.
Technology leaders turn to TrustiPhi
for specialized security engineering.
We’ve made [hundreds of] millions of devices safer. Today, billions more need hardware-level security – and simpler ways to manage that security and make it profitable.
ARCHITECTURE AND DESIGN
Chip-level, system-level and platform-level security architecture and design for: mobile, embedded, control, appliance, gateway, PC, server and connected devices
- Secure protection mechanisms and cryptographic solutions for data-at-rest, data-in-transit and data-in-process
- Platform security subsystem design, testing and validation
- Provisioning solutions for secure
supply chain management
TECHNOLOGY INTEGRATION
Device drivers – security & cryptographic peripherals, biometric sensors, smart cards, secure elements, and more. TrustiPhi has the engineering know-how to take you from product security architecture to market readiness.
- Micron Authenta
- Biometric sensor identification systems
- Platform anti-subversion mechanisms
- Hardware Security Modules (HSM)
- Trusted Platform Module (TPM)

DEVELOPMENT SERVICES
Security software and firmware that shipped on hundreds of millions of systems worldwide, including Windows, Linux, RTOS, Android, iOS and non-OS environments. Your solutions are built securely, on time and under budget. Our development services include:
- Security architecture implementation
- Embedded firmware development
- Middleware development – platform, client and server level
AUTHENTA INTEGRATION
Simple, affordable, low-risk steps to enable and easily manage security in “fleets” of IoT devices, from manufacturing through deployment, and the operating life of a device.
Today, you can select Micron Authenta, which integrates security functions into flash memory that fits into a standard socket, as the “zero component” security solution for your endpoint products. We’ll take it from there.
The more critical the industry, the sharper the need for hardware-based security in IoT devices.
Industries We Serve
Defense / Aerospace
The ability to block rogue malware from being loaded, to update in the field with security and assurance, and to constantly monitor device integrity, are vital requisites for defense-related products.
Vulnerabilities exist in numerous systems in civilian and military aviation which can be better protected with hardware-based security.

Energy Production and Utilities
Smart power meters and security sensors at remote locations need the ability to verify they have not been tampered with – as well as cyber resilience to securely reboot and resume operation despite a breach.
Communications
As modern life becomes increasingly operable from a mobile phone, and more services requiring security are accessed from a cellphone, hardware security is needed to fill the security gaps presented by a vast number of unregulated mobile apps.

Transport
Hardware-level security is essential to the sensor-based safety features of today’s vehicles, and the autonomous vehicles that will soon be on the road.
Manufacturing and Supply Chains
Protecting the integrity of devices and products through the supply chain and from the factory / assembly floor to deployment, is of paramount importance.
Industry leaders engage TrustiPhi to accelerate their security processes
Hackers from adversarial nation-states to organized cyber-Mafia are busy exploring their profit opportunities, made available through deployment of billions of IoT connected devices that lack adequate security.
In both retrofit and new products, well-chosen hardware-level security can open up a remarkable opportunity to transform products from one-time sale units to ongoing revenue streams, as their data output or operation can add new value – with one caveat: boot up, day-to-day operation, software downloads and firmware updates must be secure and based on Roots of Trust.