In this Tech Tech hosted by Micron, Ari Singer, CTO of TrustiPhi, talks engineers and product design teams through the security advantages of Authenta and how to use Triathlon to manage Authenta security in enabling new products, services, and business models.
TrustiPhi demonstrates Triathlon™ for Micron® Authenta™ at Embedded World
June 21-23, 2022: TrustiPhi joined the Authenta team and other Micron partners in Nuremberg to show how hardware-level security for IoT devices, enabled by Authenta flash memory, can be easily deployed and managed at scale, using the Triathlon platform for IOT Security Management.
SanCloud Delivers Micron® Authenta™ IoT Cybersecurity Breakthrough with TrustiPhi Integration
Strong hardware-level IoT device security that can be easily deployed and managed at scale
SOLON, Ohio, and MANCHESTER, UK, June 1, 2022 /PRNewswire-PRWeb/ — SanCloud and TrustiPhi have announced the integration of TrustiPhi’s Triathlon™ platform into SanCloud’s SanTrack™ IoT Web Platform for the management of Micron® Authenta™’s cybersecurity capabilities in SanCloud devices. This move takes advantage of Authenta’s recent integration into Triathlon, providing an unprecedented simplifying and enabling of trusted IoT services and transforming Authenta into a plug-and-play security solution. The powerful combination of all three platforms will allow SanCloud to address the growing cybersecurity demands of its industrial, factory automation and automotive customers for strong hardware-level IoT device security that can be easily deployed and managed at scale. Read more…
TrustiPhi announces Triathlon™, the IoT Security Management Platform for Micron Authenta™
Triathlon Will Enable OEMs and Device Operators to Easily Deploy Fleets of Micron Authenta-Equipped IoT Devices and Securely Manage Their Life Cycle
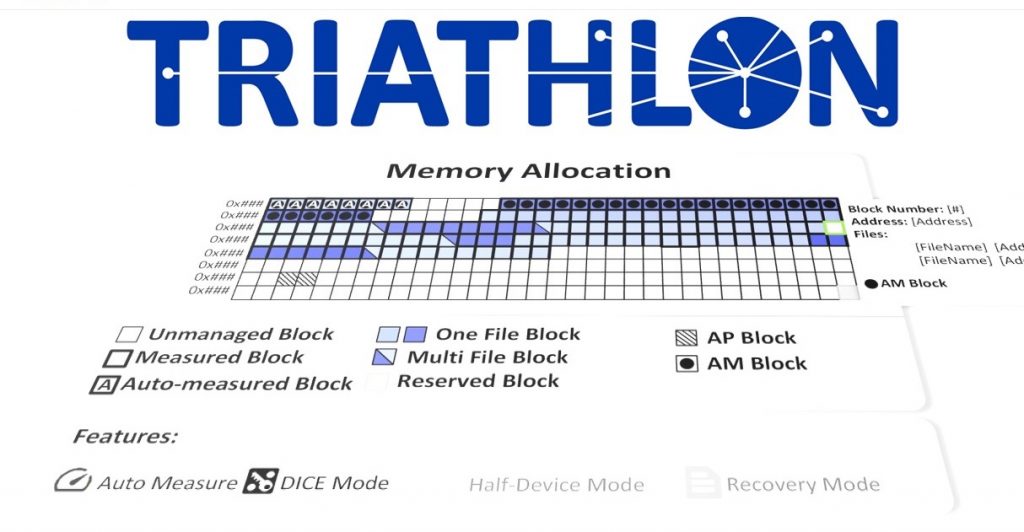
August 27, 2021 – TrustiPhi today announced its Triathlon(TM) for Micron Authenta(TM) solution for manufacturers and OEMs of endpoint products, operators of Internet of Things (IoT) device fleets, and providers of services that require hardware-level device security. Triathlon, designed as the IoT security management platform that Puts Authenta Into Action, makes it easier and simpler to overcome the global challenge of the insecure IoT by incorporating Micron AuthentaTM into new products and leveraging its capabilities to meet compliance requirements, harden devices against tampering, safeguard IoT device fleets, and make new services and business models feasible. Read announcement…
In the Press
TPM Fail: What It Means and What to Do About It
Published in Dark Reading
By Ari Singer, CTO, TrustiPhi
In November 2019, researchers led by a team at Worcester Polytechnic Institute disclosed details of two new, potentially serious security vulnerabilities — dubbed TPM Fail — that could allow attackers to steal cryptographic keys protected inside two types of Trusted Platform Modules (TPMs). Because millions of deployed systems probably have the TPM Fail vulnerability, the scope of exposure is… Read More
How Can We Make Election Technology Secure?
Paper ballots, defense in depth, and hardware-level security are all key
Published in Dark Reading
By Ari Singer, CTO, TrustiPhi and Ives Brant
Let’s go back to November 5, 2019:
In November 2019, a year before the presidential election, in Northampton County, Pennsylvania, a candidate for judge, Abe Kassis, came up with just 164 votes out of 55,000 cast — a statistical absurdity. After hand scanning the ballots from the county’s new ESS ExpressVoteXL machines, that outcome was reversed, and Kassis emerged as winner. This was no case of “disinformation warfare” and nobody alleged voter fraud nor mishandling of ballots by election workers — so what happened? Read more
5 Measures to Harden Election Technology
Voting machines need hardware-level security. The stakes are the ultimate, and the attackers among the world’s most capable.
Published in Dark Reading
By Ari Singer, CTO, TrustiPhi and Ives Brant
This article, second in a two-part series, looks at concrete, common-sense steps to make our election technology a harder target, even for the world’s best-resourced hackers. While writing this series, although TrustiPhi has worked directly to help makers of voting technology boost their security, we did reach out to recognized experts for their perspective. An unexpected twist: one of our calls landed directly in one authority’s teleconference with a Hollywood scriptwriter seeking background and ideas. This expert observed wryly that no Hollywood script could capture the dramatic and pressing need to harden election technology against attack. Read More…
8 Surprises about Trusted Platform Modules (TPM)
Trusted Platform Modules are well-understood by few people. Learn about the most important misconceptions.
Published in IoT World Today
By Ari Singer, CTO, TrustiPhi and Ives Brant

This article, first in a two-part series on TPM technology, explains some of the most important misconceptions and delivers the facts on trusted platform modules. Written by one of the world’s leading experts on TPM. Think TPM provides secure boot? Think again. Read More…
_